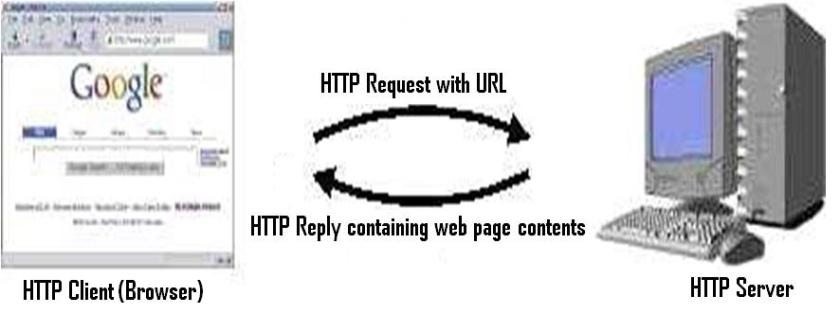
- HTTP is a standard text based, application layer protocol, used by all browsers to access millions and millions of web pages, stored across the entire globe.
- It is similar to FTP in some aspects as it uses TCP as the underlying transport layer protocol to transfer files and supports methods like get and put for data transfer. However, HTTP uses just a single TCP connection compared to two TCP connections used by FTP (one control and one data). HTTP is also similar to SMTP in the structure of protocol messages.
- HTTP is a reliable protocol, making sure that all data transferred through it reaches the peer machine without any loss. Due to this reliability requirement, HTTP uses TCP as the transport layer protocol.
- It is a simple Client-Server REQUEST-REPLY protocol, where clients send HTTP requests and servers respond with HTTP replies.
- HTTP is a stateless protocol as each HTTP Requests and Replies are treated independently by the client and server. So server does not maintain any specific state about each HTTP transaction.
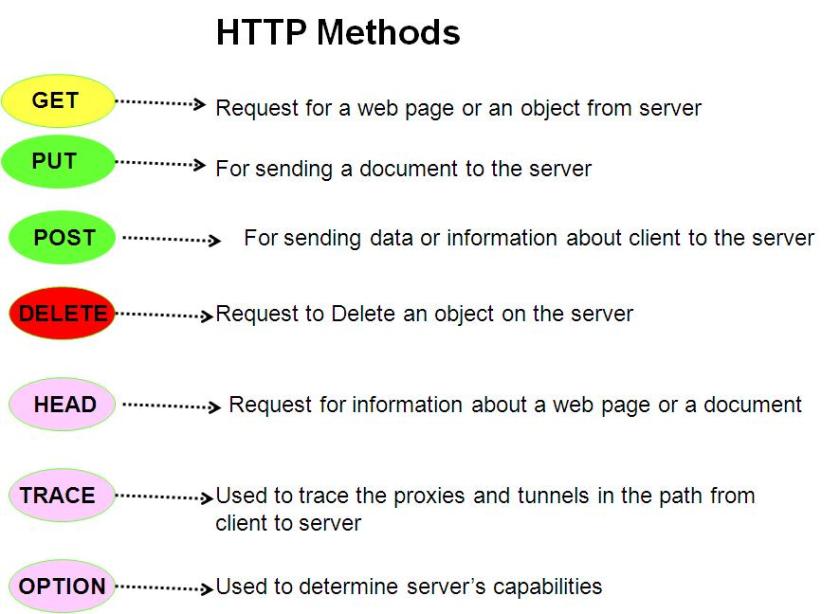
- HTTP supports multiple basic operations in the form of different HTTP methods like GET/PUT/POST/HEAD etc. The functions of some of the basic HTTP methods are given in the diagram below:
- HTTPS is a secured version of the protocol. It uses SSL protocol to send encrypted data
Methods to speed up HTTP transfers
HTTP Persistent Connections :
A HTTP reply usually consists of multiple objects (text, multiple image files etc.). In a non-persistent HTTP connection, a separate TCP connection is used for transferring each object, whereas in a persistent HTTP connection, a single TCP connection is used for transferring multiple objects, one after the other. With persistent connections, the HTTP server does not immediately close the TCP connection after sending a HTTP response in response to the initial HTTP request for a web page.
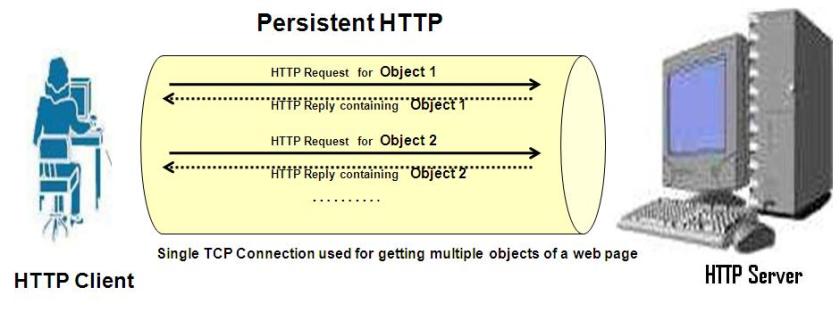
This way, further HTTP requests and responses can reuse the same TCP connection, for transfer of other objects belonging to the same web page . HTTP 1.1 supports persistent connections by default.
HTTP Pipelining
Since each web page consists of multiple objects, a separate HTTP request has to be sent by the client to the server for getting each object. Without the HTTP pipelining feature, clients issue new request only when previous response has been received. To expedite the transfer process, the HTTP pipelining feature was introduced, where client sends HTTP requests as soon as it encounters a new referenced object in the web page. With pipelining, clients send new HTTP requests without waiting for HTTP responses of previous requests, thereby optimally using the network resources and expediting the web page tranfer, by sending multiple requests simultaneously.
HTTP Proxy
HTTP proxies are intermediate machines that are stored closer to the HTTP clients, to expedite HTTP tranfers. HTTP proxies locally cache frequently accessed pages and serve multiple clients. The HTTP proxy caches a copy of the HTTP reply, whenever a client machine accesses a new web page. Subsequently, if a HTTP request is sent for the same web page (either by the same client or by a different client), the HTTP proxy checks with the HTTP server whether the web page version held by it is latest. If yes, the HTTP proxy sends back the HTTP response to the end client using its cached copy. Otherwise, it gets the updated page from the actual web server, updates its local cache and then replies to the client. HTTP proxies thereby serves the double purpose of conserving network bandwidth and also expediting web page tranfers.
HTTP Cookies
A HTTP cookie is basically an entity used by HTTP servers to track a specific user. When a new user or a new computer accesses a web page for the first time, the web server creates a cookie for that user and sends it back as part of the HTTP reply. The cookie is a collection of information about that user (like name, address, domain name etc.). The cookie sent by the server is stored in the local browser cache by the browser. Whenever the user accesses the same HTTP server again, the browser additionally sends the cookie as an additional parameter in the HTTP Request. The server uses this cookie to uniquely identify the user and may customize the HTTP Reply (web page contents) based on that user’s preferences. Cookies can be used for multiple purposes like tracking user’s preferences and serving web content adaptively, giving access to web pages only for authenticated users, for electronic shopping etc.