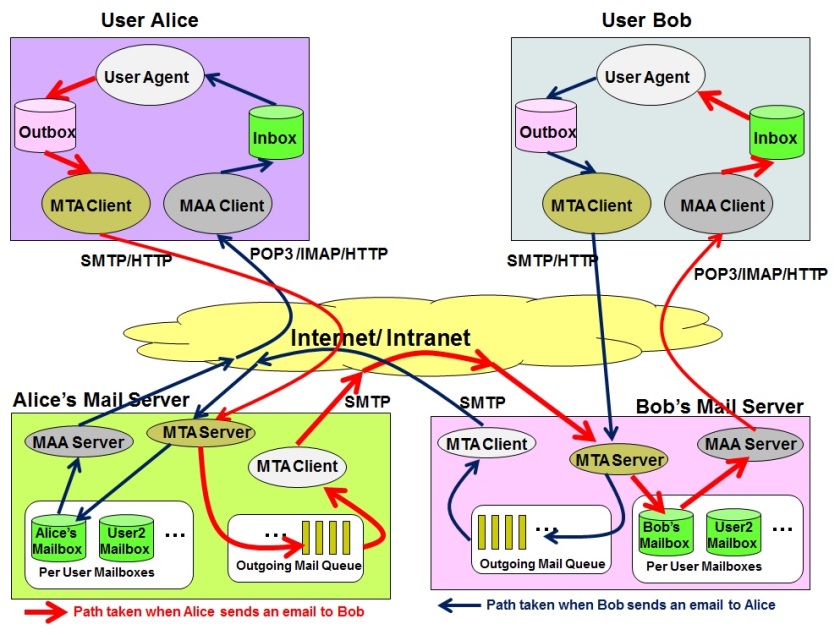
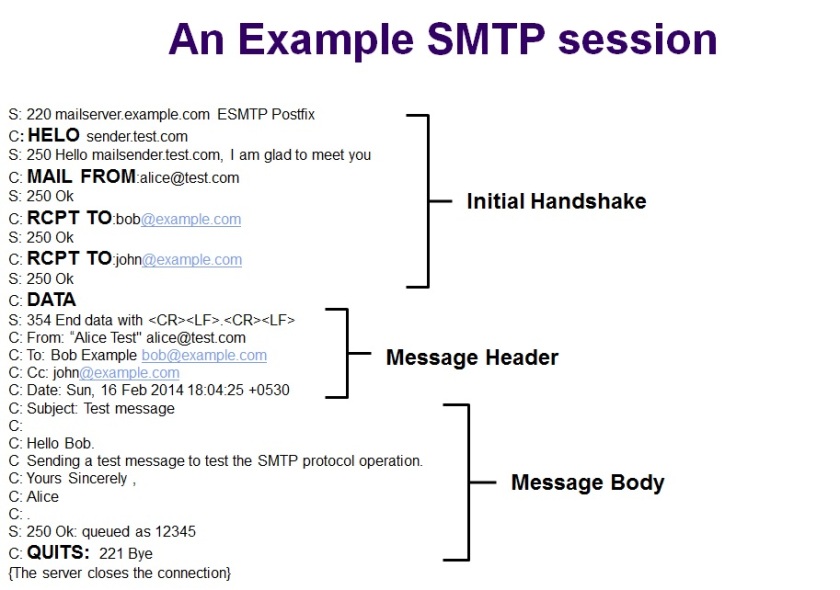
This post gives a basic overview of the Simple Network Management Protocol (SNMP) and also an overview of its related protocols MIB (Management Information Base) and SMI (Structure of Management Information).
SNMP is the most widely used and popular protocol for managing, monitoring and controlling of network devices like routers, switches over a public or private network. SNMP is not only a protocol, but a framework for controlling and monitor multiple network devices. SNMP, with two other closely related protocols, namely SMI and MIB, work in unison to achieve this.
Basic Theory of Operation
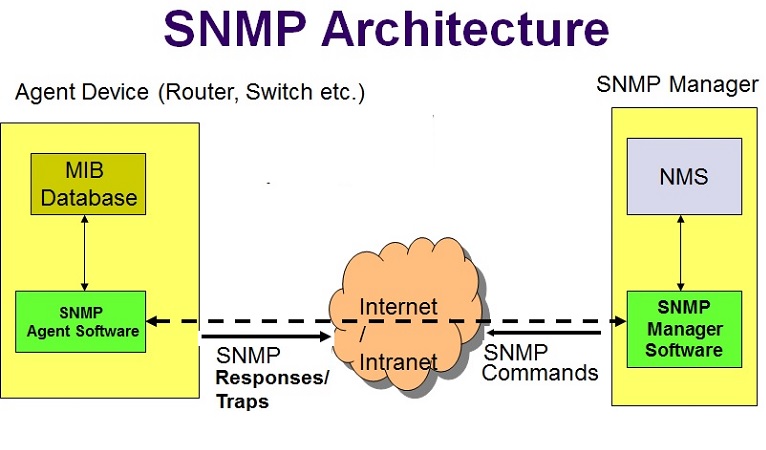
A wide range of network device parameters like system uptime, interface status, interface packet statistics, routing protocol statistics etc. are treated as different objects by SNMP. These objects are maintained by the server portion of SNMP software, known as SNMP agent, running on network devices like routers and switches. A SNMP client program known as the SNMP manager, runs on a remote machine and queries these objects, through SNMP Get requests, to know the status of the network device. Similarly, the manager can control some of the network device parameters by doing an SNMP Set request which is equivalent to a write operation ( e.g. to reset a router or shutting down an interface of a router). Apart from the manager sending SNMP GET/SET requests to the agent, the agent too can proactively notify the manager of critical/significant events on the network devices through SNMP TRAP messages. Thus, SNMP manages the device by reading and writing values to different SNMP objects, with each object representing a specific network parameter. This is the basic theory of operation of SNMP and is shown in the diagram given below:
Roles of protocols SMI, MIB and SNMP
While SNMP is the basic carrier protocol used on the network, for sending object Get and Set requests, a second protocol named as SMI is used to define the rules/framework for naming the objects, defining the permitted object types and also for specifying the object encoding method for transmission. A third protocol named as MIB, specifies the actual set of objects for different network device protocols/entities (e.g. System MIB, Interface MIB, IP MIB, TCP MIB, UDP MIB etc.). The MIB also specifies the type of each object used within a MIB file (it has to be one of the standard object types defined by SMI) and also the relationship between the different objects belonging to the same network protocol/entity.
The role of these three protocols is summarized in the diagram given below:
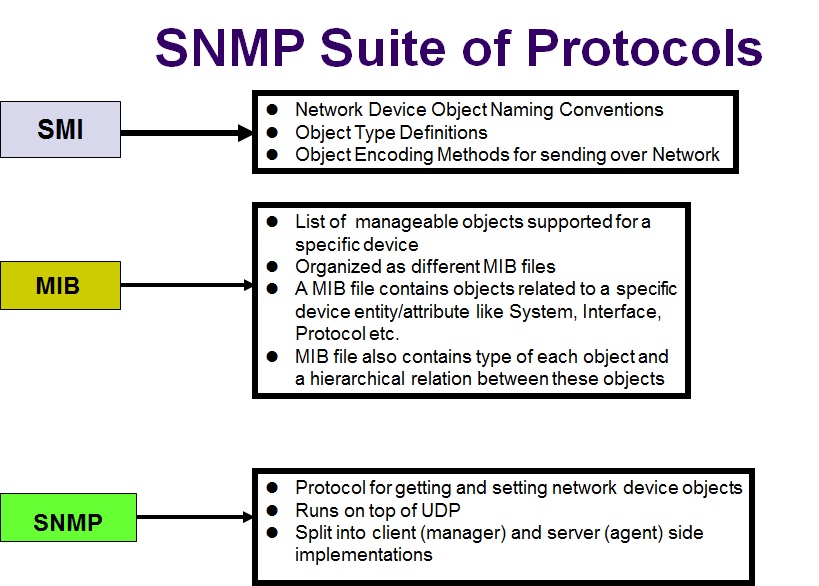
A summarized description of each of these protocols is given below:
SMI
SMI protocol is basically used to standardize the different object attributes like object Identifiers, object type and encoding methods for objects.
- Object Identifiers: Each SNMP object has a unique object identifier. SMI permits object identifiers to be either in name form (e.g. iso.org.dod.internet.mgmt.mib-2) or in number form (e.g. 1.3.6,1,2,1). Note that both forms have a hierarchical structure.
- Object Types : As for object types, SMI defines both standard types like integer, octet string etc. and non-standard network specific types like IP address, Timeticks etc.
- Object Encoding Method: SMI uses the Basic Encoding Rules (BER) method consisting of type/tag, length and value, to encode objects along with their values, for transmission inside SNMP packets.
- SMI does not specify the list of objects for a specific network protocol/entity nor does it specify the type of objects to be used for a specific network protocol. These aspects are taken care by MIB.
MIB
MIBs enable representation of device parameters in a standard format.
MIBs are nothing but the actual set of objects supported by a network device, for controlling and monitoring by the SNMP protocol.
These objects are classified and separately maintained in different MIB files. There would be a separate MIB file maintained by the SNMP agent on the network device, for each protocol/entity that can be managed by SNMP (e.g. System MIB, Chassis MIB, IP MIB, TCP MIB, UDP MIB, ICMP MIB, Interface MIB etc.).
MIBs are organized in a tree like structure and each MIB variable has a unique object ID
Each MIB file define three things, namely
- List of objects supported for a specific protocol/entity
- Type of each object
- Hierarchical relationship between all the objects of a given protocol/entity
For e.g. UDP MIB would contain objects like udpInDatagrams (denoting number of incoming UDP datagrams to the device), udpOutDatagrams (denoting number of outgoing UDP datagrams out of the device) etc. The UDP MIB would also specify the type of these objects (for e.g. udpInDatagrams and udpOutDatagrams could be of type Integer). The UDP MIB could also contain a UDP Table consisting of the set of all current UDP socket connections handled by the device at that instant of time. The entries in this table have a child relationship to the parent UDP table, which means that MIB files maintain a hierarchical relationship between the different objects pertaining to a specific network protocol/entity.
SNMP
- Is an application layer, client-server protocol, specifically designed for Network management/monitoring purposes
- Is MIB based and runs on top of the transport layer protocol UDP
- SNMP mainly supports GET and SET operations on a wide variety of device parameters/MIB objects
- Requires an SNMP agent component to be present in the network device that is to be managed
- A SNMP manager component runs on remote management stations to talk to SNMP agents
- A single manager usually monitors multiple network devices/agents
- Devices can be configured and monitored remotely as long as they have IP connectivity
- Get, Get-Next, Get-Response, Get-Bulk, SET, TRAP, INFORM are some of the standard methods supported by SNMP
- Traps enable agents to inform managers about important events like alarm triggering, interface down, routing table changes etc.
- Vendor specific extensions in the form of private MIBs makes SNMP customizable so that any new protocol/feature/parameter of a device can be managed through SNMP
- Recent versions of SNMP support security too, so that SNMP messages are sent in encrypted form using standard encryption techniques over the network.
- While a SNMP agent waits on the reserved UDP port 161 for receiving SNMP requests from SNMP managers, SNMP managers wait on the reserved UDP port 162, for receiving SNMP Trap messages from SNMP agents.