UDP Properties:
- Is a light-weight connection-less protocol that runs on top of IP
- Provides an end-to-end, process to process communication mechanism for peer applications to communicate
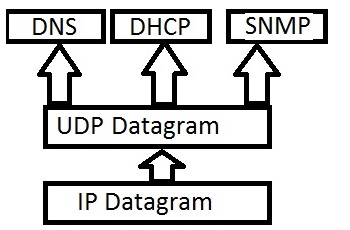
- Provides basic application layer process multiplexing and de-multiplexing services through UDP source port and destination port number fields, as shown in the diagram below
- Supports a checksum feature for error detection purposes but this feature can optionally be disabled.
- Does not have the concept of peer acknowledgment and hence unreliable
- Does not support flow control and congestion control. Applications using UDP have to take care of flow/congestion control
- Is best suited for applications that require fast data transfer but can tolerate slight loss of data
- Is the preferred transport layer protocol for IP multicasting and real-time audio, video, multimedia applications, where fast delivery is more important than reliability
- Is also used by simple client-server based application layer protocols where a quick response is required from a server, for a client request, without the overhead of connection establishment procedures (E.g. DNS, SNMP etc.)
- Popular application layer protocols like SNMP, DNS, TFTP, RTP use UDP as the transport protocol
Basic Theory of Operation of UDP
UDP is just a simple extension to IP datagram service, where it provides application multiplexing and checksum computation of application data on the sending end and application de-multiplexing and checksum verification on the receiving end. It is a connection-less service, with no support for reliability, flow control and network congestion control.
UDP Encapsulation and Decapsulation
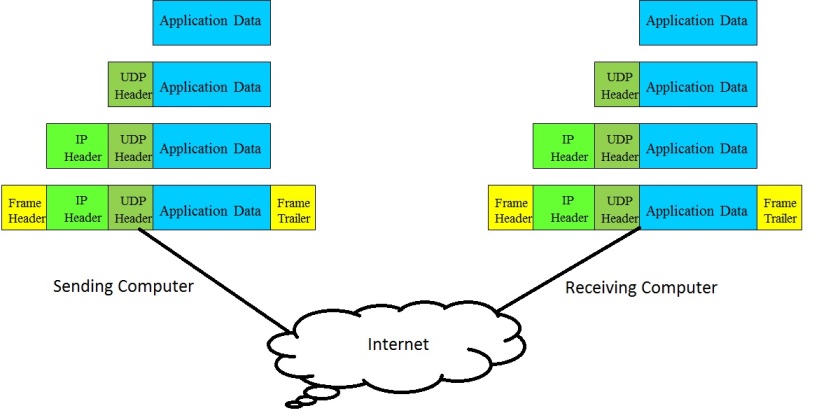
To achieve this, at the sending computer end, the UDP stack encapsulates each piece of application data with a UDP header consisting of source and destination port numbers, apart from adding a checksum.
The UDP receiving process at the peer receiving end does the reverse operations. It first verifies the checksum to make sure that the UDP datagram came through the network uncorrupted and then uses the destination port number field to de-multiplex and hand over the application data to the appropriate application layer process.
UDP does not segment the incoming application data into streams of bytes. Hence, it is the responsibility of the application to segment the data as message blocks before handing it over to UDP layer.
Also the UDP layer at the receiving end drops erroneous UDP datagrams detected through checksum verification and it also drops UDP datagrams if there is no additional UDP buffers for storing it. In such cases, it does not inform the sender of dropped frames. Also there is no concept of UDP datagram numbering or acknowledgement. It is up to the application layer to take care of all these problems.
UDP Header and UDP Pseudo Header
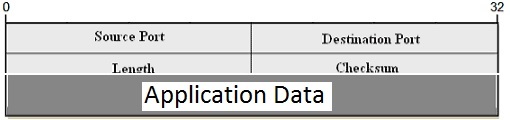
The UDP header is a simple one consisting of just 8 bytes and includes only 4 fields. They are the source port number, destination port number, a length field specifying the length of the whole UDP datagram including the UDP Header and a Checksum field for error detection purposes, as given in the diagram below:
UDP Pseudo Header
UDP uses the whole UDP datagram and some fields from the IP header (termed as pseudo header) for computing the checksum, as shown in the diagram given below.
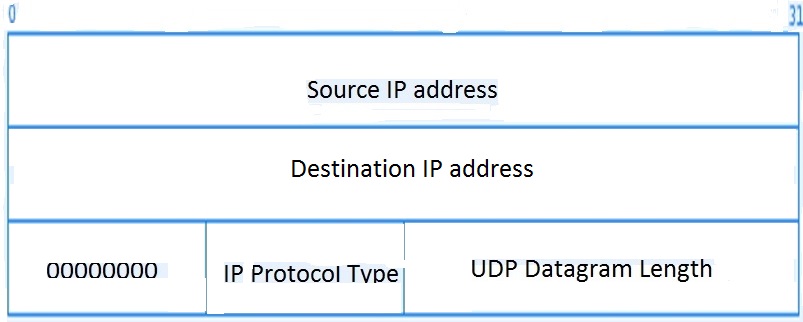
The reason for including the pseudo header is to verify that the UDP datagram is delivered to the right destination computer, as sometimes the IP header may get corrupted and the UDP datagram may arrive intact at the wrong destination. The fields of the Pseudo header include the source and destination IP address of the IP packet that carries the UDP datagram, the IP protocol type field (UDP with a value of 0x11) and the total length of the UDP datagram.